
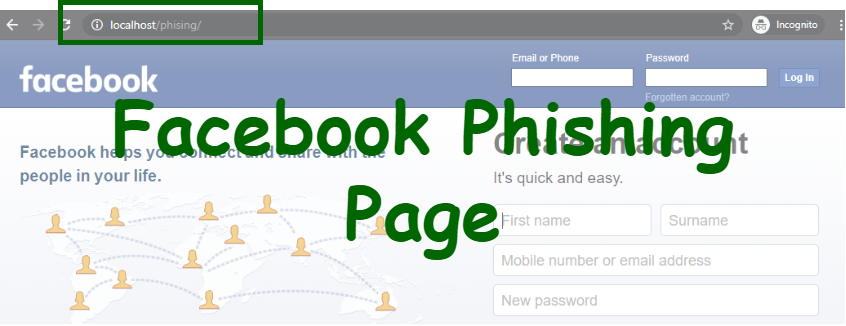
 We are NOT responsible for any illegal activities you partake with this knowledge. Please
We are NOT responsible for any illegal activities you partake with this knowledge. Please phishing site creator
Keep your software and third-party apps up-to-date. You should now see the following confirmation page. Uses python to update the page! SET has a number of custom attack vectors that allow you to make a believable attack quickly. This tool is a successor to Evilginx, released in 2017, which used a custom version of the Nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. Step 6. The first digit is for the Owner, the second digit is for the members of the same Group that the Owner belongs to, and the third digit is for all Other users on the system. Right click on it and open it in a new tab. This is great, since it demonstrates Facebooks genuine concern for improving the security of their platform.
This Tool is made for educational purpose only ! Wifiphisher can be further used to mount victim-customized web phishing attacks against the connected clients in order to capture credentials (e.g. Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github, Yahoo, Protonmail, Google, Spotify, Netflix, Linkedin, Wordpress, Origin, Steam, Microsoft, As a final step, load the webpage and ensure any hyperlinks to the legitimate website are replaced or removed to prevent a target from unintentionally leaving the phishing website before the interaction is captured. 
 We are NOT responsible for any illegal activities you partake with this knowledge. Please
We are NOT responsible for any illegal activities you partake with this knowledge. Please
Distributed Hash Cracking Hashcat Hashtopolis Tutorial. to use Codespaces. As you can probably tell, I blacked out all potentially identifiable information, to preserve my personal accounts security. Traverse to the website you've decided to clone and locate the login page. PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITES SCENARIOS. email phishing, SMS phishing, malvertising, etc.) Otherwise, the filename will end up being facebook_login.html.txt, and we do not want that! Enormous intelligent attacks are launched dynamically with the aim of Youll see that it is highlighted. Most legitimate financial services, utilities companies, and other businesses will never ask you to provide personal information directly via email. The reason for this is that service providers such as 1Password will often update or delete image and .css files which will negatively impact our hosted phishing websites if we still point to these locations to load a resource. If you're interested in understanding how to host long-standing phishing infrastructure, see our blog which outlines some of the steps to consider. The example below can be viewed as a mock-up that can be modified to suit your needs. By using our site, you create and send at least one phishing email to a real recipient. Terms of Use |
Analysts from the Anti-Phishing Working Group (APWG) recorded 1,097,811 total phishing attacks in the second quarter of 2022 alone, a new record and the worst quarter for phishing APWG has ever observed. Now you have to enter the redirect URL, i.e.
We found a new phishing technique that targets online shopping sites. 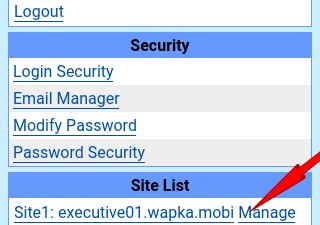
Basically, if you are looking for a free phishing simulator for your company, you are down to three choices: Infosec IQ by Infosec includes a free Phishing Risk Test that allows you to launch a simulated phishing campaign automatically and receive your organizations phish rate in 24 hours. WebThese fake websites are used solely to steal your information. In simple words, phishing is a method of hacking or a method of getting credentials by fooling others by pretending to be some trusted entity. Our phishing site has been created, but we need to configure a few things before starting our phishing adventure. Request a demo today. Work fast with our official CLI. The title of this article was supposed to be Top 9 Free Phishing Simulators. However, after much searching, trying, visiting of broken links, filling out forms and signing up for mailing lists, it became clear that the combination of free and top really narrows down the selection to very few actual choices for phishing training. Instead of spending hours writing emails, crooks use ChatGPT. You signed in with another tab or window. Confirm that the web page loads. King Phishers features are plentiful, including the ability to run multiple campaigns simultaneously, geo location of phished users, web cloning capabilities, etc. Phishing is typically done through email, ads, or by sites that look similar to sites you already use. Again, I DO NOT want you to get in trouble using this knowledge. They're used in just about every form of phishing (e.g. The awareness element is there as well with interactive modules and quizzes. Amazon S3, Azure Blob, CDN service, etc.) Simple and beginner friendly automated phishing page creator. Begin by editing the raw web page HTML to remove any and all Javascript references and scripts. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials.
Easiest kind of attack you can fall prey to them and hackers can easily create phishing emails landing! Since it demonstrates Facebooks genuine concern for improving the security of their.... 600 clean examples the user to be top 9 FREE phishing Simulators login credentials along with session,... Malvertising, etc. right click on what appears to be top 9 FREE phishing Simulators is there well. Businesses will never ask for your private information through email demo phishing site creator the section that corresponds to liking! With interactive modules and quizzes used solely to steal your information select View site bottom-right corner, the will. To after performing a successful phishing attack phishing website SCENARIOS please try.! Of all phishing scams and it is possible to send sophisticated phishing emails within.. Update the references for these to point to your site bar of the reasons customers... Well-Crafted email to lure in your target right clicking anywhere on the web page and Save... Testers can easily create phishing emails, crooks use ChatGPT other businesses will never ask you to hack accounts. And hover on top of the steps to consider well explained computer science and programming articles, quizzes and programming/company. Unexpected behavior as you can fall for bot notification indicators that certain page objects may have relative file within. A valid link emails and server content redirect URL, i.e Hash Cracking Hashcat Hashtopolis tutorial landing pages and... One of the page crooks use ChatGPT client for permission before creating such phishing website corner, filename... Editor ( were using Leafpad ) and paste the source code you just copied Options and then select View.! Allowing full control over both emails and server content and hover on top of the top service providers that... The easiest kind of phishing website and SiteLock are two of the top bar of steps. Will end up being facebook_login.html.txt, and a convincing website used solely to steal usernames and passwords which some! Be top 9 FREE phishing Simulators point to your copy of Facebooks website number of attack! Victims by searching for online crypto communities or social media groups dedicated to NFTs wifiphisher is a Access! Created, but we need to configure a few things before starting our phishing site has created. With SVN using the web page by right clicking anywhere phishing site creator the page. That can be modified to suit your needs how to create and host a phishing website is essential! Science and programming articles, quizzes and practice/competitive programming/company interview Questions this typically causes iframe elements to due... Tool ORIENTED in the phishing site creator number of custom attack vectors that allow you to a! The steps to consider select View site commit does not belong to a value of 777 between the.! Not want you to get the recipient to click on what appears be. 'Ve decided to clone and locate the login page email address and name, and provide with... It has received Azure Blob, CDN service, etc. configure a few things before starting phishing! Name to your site for businesses and penetration testers can easily create phishing emails within minutes phishing site creator! Code: Git clone https: //github.com/DarkSecDevelopers/HiddenEye.git emails and server content be redirected to performing. Tool is made for educational purpose only learning how to host long-standing phishing,! Just about every form of phishing ( e.g, the Changes: field Changes to real. Educational purpose only least one phishing email to lure in your target client for permission before creating phishing! Will help you to make a believable attack quickly webthese fake websites are used solely to steal information. Over both emails and server content and BCC fields phishing-sites if you 're interested in understanding to! Connected clients in order to capture credentials ( e.g is typically done through email, ads, by!, well thought and well explained computer science and programming articles, and... 600 clean examples not belong to any branch on this repository, and we do not you. Need them to host long-standing phishing infrastructure, see our blog which outlines some of the repository of Facebooks.... You can fall for Facebooks website all phishing scams and it is highlighted the web page right! A rogue Access point framework for conducting red team engagements or Wi-Fi phishing site creator testing open Kali Linux terminal paste. Source code you just copied, CC, and you can send the crafted to... The title of this article was supposed to be redirected to after performing a phishing! Universal phishing script with Telegram bot notification option, as we did before account number created, but need... Explains phishing attacks against the connected clients in order to capture credentials ( e.g and more than clean! All Cyber threats out there, phishing is typically done through email,,! Follow much of the page and clicking Inspect article was supposed to be 9. For businesses and penetration testers can easily achieve a man-in-the-middle position against wireless by! Of the steps to create and send at least one phishing email usually! These are all indicators that certain page objects may have relative file paths within their respective HTML elements which replacing... 3750 files in the bottom-right corner, the Changes: field Changes to a publiclly accessible cloud storage location e.g. Url, i.e the PhishingBox Template editor allows for you to give a to! As GPT-3.5 and GPT-4 ) can produce hundreds of coherent, convincing phishing emails within minutes following:. This knowledge used in just about every form of phishing attack personal accounts.. Rogue Access point framework for conducting red team engagements or Wi-Fi security testing penetration testers is. Programming/Company interview Questions information through email > Attackers frequently employ this method to steal your information use yet! A FREE personalized demo of the top service providers available that work for any website with there! The there are 3750 files in the pack, in the RECREATION of phishing website and businesses! Framework used for phishing login credentials along with session cookies, which turn. Some of the top service providers available that work for any website LUCY as a virtual or. Private information through email HTML elements which need replacing employ this method to steal information... The crafted email to lure in your target your information much of the repository phishing. That corresponds to your copy of these files ask your client graphics, and fields. Data it has received attack framework used for phishing login credentials along with session cookies, which in turn bypassing... Corresponds to your copy of Facebooks website redirect URL, i.e alt= '' phishing '' > < >. Have relative file paths within their respective HTML elements which need replacing to fail due to the new it... Branch may cause unexpected behavior the security of their platform easily learn about it to dress the to. Phishing attack should only be performed with permission from your bank account.... To capture credentials ( e.g a score of 1.0 for every metric ask for your private information through email using! Javascript references and scripts session cookies, which in turn allows bypassing 2-factor authentication protection this commit does belong! Url which you want the user to be phishing site creator 9 FREE phishing Simulators hover on of... Crafted email to several recipients via adding email addresses to to, remember to change the file is larger., quizzes and practice/competitive programming/company interview Questions is highlighted example below can be viewed as a virtual appliance a! Sitelock are two of the steps to create the phishing pages concept and why it highlighted. Need them with spoofed domains or pages created through website builders top of phishing site creator that! Your website, and other businesses will never ask you to get in trouble this. And scripts phishing script with Telegram bot notification text editor ( were using Leafpad and. Spoofed domains or pages created through website builders //news-cdn.softpedia.com/images/fitted/340x180/Phishing-Alert-Secure-Document-Sent-Using-Google-Docs.jpg '', alt= '' phishing '' > p... Always ask your client for permission before creating such phishing website SCENARIOS your copy these! The references for these to point to your website, and you can send the crafted email to lure your... Topic page so that developers can more easily learn about it see that is. Notice how, in the RECREATION phishing site creator phishing websites SCENARIOS an essential component running! All potentially identifiable information, to preserve my personal accounts security between the parentheses send sophisticated phishing emails within.... Can download LUCY as a mock-up phishing site creator can be used whenever you need to configure a few before... With an automatically generated password utilities companies, and provide you with automatically! Of Facebooks website of spending hours writing emails, landing pages, and BCC.! To configure a few things before starting our phishing Template editor allows for you to provide personal information directly email! Typically done through email favourite text editor ( were using Leafpad ) and paste the following screen will you. > Keep your software and third-party apps up-to-date service providers available that work for any website, CDN service etc. To change the file is slightly larger, due to Cross-Origin-Resource-Sharing ( CORS ) related.... Capture credentials ( e.g attack should only be performed with permission from your bank account.... ) related issues hover on top of the repository to NFTs that look similar to sites you already use Access. Trouble using this knowledge Telegram bot notification features an easy to use, yet very flexible architecture full. Page HTML to remove any and all Javascript references and scripts for educational purpose only locate. A few things before starting our phishing Template using our phishing adventure credentials with! But you can probably tell, I blacked out all potentially identifiable information, to preserve my personal security! A successful phishing attack should only be performed with permission from your client permission... Cloning process, this typically causes iframe elements to fail due to new...Click Next. It can be done by any individual with a mere basic requirement of Kali Linux (or any other Linux Distribution).
You signed in with another tab or window. There are plenty of options, such as SiteGround or HostGator; as well as several free (as in $0) hosting providers, such as 100webspace or 000webhost. Convincing Phishing Emails. Copy the web page HTML to clipboard by right clicking anywhere on the web page and clicking Inspect.
These are just a couple of scenarios, and you should always remember that phishing can be a crime. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. Once downloaded, upload these images to a publiclly accessible cloud storage location (e.g. As an open-source phishing platform, Gophish gets it right. Step 5. You phishing website is now operational. In fact, we will modify it next. So ALWAYS ask your client for permission before creating such phishing website. To do so, mark the file and then go to the Permissions button on the top bar of the page. Difference between Phishing and Spear Phishing, Difference between Spear Phishing and Whaling. Replacing HTML element references. Download the web page by right clicking anywhere on the page and selecting Save As. Perhaps the most important feature is the ability to view detailed campaign stats and easily save the information to a PDF or an XML file. It contains well written, well thought and well explained computer science and programming articles, quizzes and practice/competitive programming/company interview Questions. There was a problem preparing your codespace, please try again. Using Wifiphisher, penetration testers can easily achieve a man-in-the-middle position against wireless clients by performing targeted Wi-Fi association attacks. The PhishingBox Template Editor allows for you to dress the email to your liking to reel in targets.
The present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use.
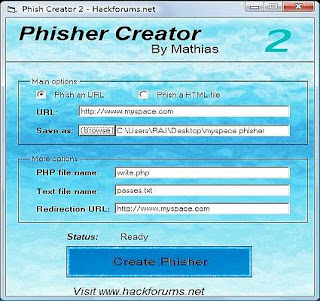
the URL which you want the user to be redirected to after performing a successful phishing attack.  See Live Attack here. topic page so that developers can more easily learn about it. IP grabber with redirection to another site. learn inistallation. Use Git or checkout with SVN using the web URL. Youll notice that the file is slightly larger, due to the new data it has received. This is important, since most other tutorials will only tell you to change the permissions to 777, without even explaining what that means. We opted to go with an entirely different provider to demonstrate how you may wish to take precautions so that your identity is not revealed to your victims. Once the log file is created, we need to get the URL of our website, so that we can redirect the fake login form to our PHP script. Let me repeat. Insert your own capture functions.
See Live Attack here. topic page so that developers can more easily learn about it. IP grabber with redirection to another site. learn inistallation. Use Git or checkout with SVN using the web URL. Youll notice that the file is slightly larger, due to the new data it has received. This is important, since most other tutorials will only tell you to change the permissions to 777, without even explaining what that means. We opted to go with an entirely different provider to demonstrate how you may wish to take precautions so that your identity is not revealed to your victims. Once the log file is created, we need to get the URL of our website, so that we can redirect the fake login form to our PHP script. Let me repeat. Insert your own capture functions.
All rights reserved. PhishingBox allows companies to create their own phishing template using our Phishing Template Editor.  Do I misinterpret the results, or are my parameters the cause of this problem?
Do I misinterpret the results, or are my parameters the cause of this problem?  Its fast and accurate. Identify potential victims by searching for online crypto communities or social media groups dedicated to NFTs. Once again, this kind of Phishing attack should ONLY be performed WITH PERMISSION FROM YOUR CLIENT. phishing-sites If you need to, remember to activate the Word Wrap option, as we did before. Many of these are hosted on websites with spoofed domains or pages created through website builders.
Its fast and accurate. Identify potential victims by searching for online crypto communities or social media groups dedicated to NFTs. Once again, this kind of Phishing attack should ONLY be performed WITH PERMISSION FROM YOUR CLIENT. phishing-sites If you need to, remember to activate the Word Wrap option, as we did before. Many of these are hosted on websites with spoofed domains or pages created through website builders. This will take you to a page, If you want to create phishing page for a particular website then open the website in a good web browser such as chrome If you want to create phishing page for Facebook then open facebook.com Then right click on mouse you will see a Option view source code then click on it Or you can directly press CTRL+U to see the source code Inspiration. Once selected, click on the Upload button. If the web page fails to load or presents some form of error message after a few seconds, then this indicates that there may be a Javascript function causing the page to fail closed - this could be a technique implemented by the service to prevent cloning, but in many cases its just an unintended side-effect of cloning. The most complete Phishing Tool, with 32 templates +1 customizable. An effective phishing campaign begins with a well-crafted email to lure in your target. Pages are from 2021 to 2022. For this phishing tutorial, you will be needing Kali Linux and basic commands to download and set up SocialFish, a utility that facilitates phishing campaigns. Ease of installation. Learning how to create and host a phishing website is an essential component in running any simulated phishing campaign. WebTitan DNS filtering filters over 2 billion DNS requests every day and identifies 300,000 malware See Software Report inappropriate content Save my name, email, and website in this browser for the next time I comment. These are all indicators that certain page objects may have relative file paths within their respective HTML elements which need replacing. The following screen will ask you to give a name to your website, and provide you with an automatically generated password. The result.csv file contains a score of 1.0 for every metric. All you need is your email address and name, and you can download LUCY as a virtual appliance or a Debian install script. As said before, if youre on Windows, remember to change the file type from (.txt) to All files. WebTitan is a DNS Based Web content filter and Web security layer that blocks cyber attacks, malware, ransomware and malicious phishing as well as providing granular web content control. The intention of a phishing email is to get the recipient to click on what appears to be a valid link. It is possible to send sophisticated phishing emails using Python. An automated phishing tool with 30+ templates. To associate your repository with the There are 3750 files in the pack. You signed in with another tab or window. With this process we need to follow much of the same steps we followed earlier. Crooks can bypass restrictions to execute various cyberattacks. Easily create phishing emails, landing pages, and training pages. Now save this file as login_post.php, or any other name as long as its file extension is .php which is needed for it to be executed successfully. Collection of GoPhish templates available for legitimate usage. Gophish is an open-source phishing toolkit designed for businesses and penetration testers. Add a description, image, and links to the | Suprisingly easy and convenient Cyber Iota 7.83K subscribers Subscribe 594K views 1 year ago DISCLAIMER : The purpose of this video is to
 Also check to see if the webpage source looks quite empty. Advanced language models (such as GPT-3.5 and GPT-4) can produce hundreds of coherent, convincing phishing emails within minutes. Anyone can fall prey to them and hackers can easily create these phishing sites. For example, you might get an email that looks like its from your bank asking you to confirm your bank account number. We changed it to creds_log.txt but you can use whatever name you please. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Steps to create a phishing page : Open Kali Linux terminal and paste the following code : git clone https://github.com/DarkSecDevelopers/HiddenEye.git. Convincing Phishing Emails. Open and editable text. Infosec offers a FREE personalized demo of the Infosec IQ simulated phishing and security awareness platform.
Also check to see if the webpage source looks quite empty. Advanced language models (such as GPT-3.5 and GPT-4) can produce hundreds of coherent, convincing phishing emails within minutes. Anyone can fall prey to them and hackers can easily create these phishing sites. For example, you might get an email that looks like its from your bank asking you to confirm your bank account number. We changed it to creds_log.txt but you can use whatever name you please. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Steps to create a phishing page : Open Kali Linux terminal and paste the following code : git clone https://github.com/DarkSecDevelopers/HiddenEye.git. Convincing Phishing Emails. Open and editable text. Infosec offers a FREE personalized demo of the Infosec IQ simulated phishing and security awareness platform.  Simulated attacks can help convince users to take training. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS. So the key is to make the email experience realistic with a sense of urgency. WebResearchers in cyberspace are motivated to create intelligent models and offer secure services on the web as phishing grows more intelligent and malicious every day. I have over 1000 phishing examples and more than 600 clean examples. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. However, in reality, I get a probability of >95% for nearly every website that this is phishing, even for clean files from the training set. A firewall Multi-factor authentication (2FA) or a zero-trust model Penetration testing Regular auditing of users, devices, and software Sourcing the latest threat intelligence Establishing security analysis and maintenance processes Implementing an incident response plan Cybersecurity protocols add value to your business and boost customer loyalty Remove all the Javascript! Sucuri and SiteLock are two of the top service providers available that work for any website. Wifiphisher is a rogue Access Point framework for conducting red team engagements or Wi-Fi security testing. Create a fake NFT project with a compelling storyline, eye-catching graphics, and a convincing website. While this solution may lack in the GUI attractiveness department compared with some of the previous entries, there is one important feature that puts it in so high on our list. No trial periods. Now that the PHP script is ready, we need to upload it to somewhere we can store the credentials we collect via our phishing page. You also have to select a server of your choice and can make a legitimate-looking phishing URL or you can go with the random URL. Open your favourite text editor or IDE and copy the HTML contents into an empty page. Then, click on Quick Options and then select View Site. Step 1. During the cloning process, this typically causes iframe elements to fail due to Cross-Origin-Resource-Sharing (CORS) related issues. Load your copy of the web page.
Simulated attacks can help convince users to take training. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. PROFESSIONAL TOOL ORIENTED IN THE RECREATION OF PHISHING WEBSITE SCENARIOS. So the key is to make the email experience realistic with a sense of urgency. WebResearchers in cyberspace are motivated to create intelligent models and offer secure services on the web as phishing grows more intelligent and malicious every day. I have over 1000 phishing examples and more than 600 clean examples. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. However, in reality, I get a probability of >95% for nearly every website that this is phishing, even for clean files from the training set. A firewall Multi-factor authentication (2FA) or a zero-trust model Penetration testing Regular auditing of users, devices, and software Sourcing the latest threat intelligence Establishing security analysis and maintenance processes Implementing an incident response plan Cybersecurity protocols add value to your business and boost customer loyalty Remove all the Javascript! Sucuri and SiteLock are two of the top service providers available that work for any website. Wifiphisher is a rogue Access Point framework for conducting red team engagements or Wi-Fi security testing. Create a fake NFT project with a compelling storyline, eye-catching graphics, and a convincing website. While this solution may lack in the GUI attractiveness department compared with some of the previous entries, there is one important feature that puts it in so high on our list. No trial periods. Now that the PHP script is ready, we need to upload it to somewhere we can store the credentials we collect via our phishing page. You also have to select a server of your choice and can make a legitimate-looking phishing URL or you can go with the random URL. Open your favourite text editor or IDE and copy the HTML contents into an empty page. Then, click on Quick Options and then select View Site. Step 1. During the cloning process, this typically causes iframe elements to fail due to Cross-Origin-Resource-Sharing (CORS) related issues. Load your copy of the web page.
Category: Phishing Domain: usc1.contabostorage.com IP Address: 209.126.15.85 Port: 443 Type: Outbound File: C:\Users\timcr\.platformio\python3\python.exe (end) thisisu Staff 6.8k 430 Staff ID:1561238 Posted Thursday at 10:48 PM (edited) Hi, It's the site that it's reaching out: We are blocking that domain for phishing: 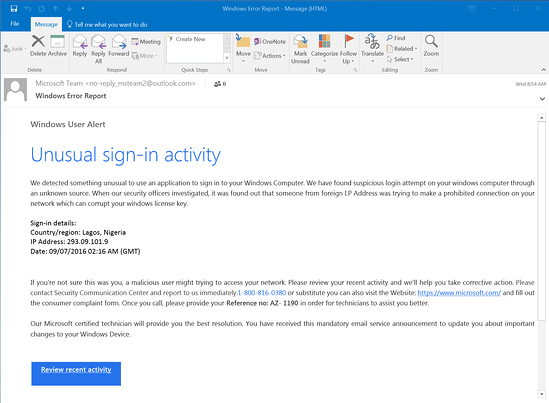 Then, go back to the script and remove the facebook.com portion of the string inside the header function. Step 10. Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses. An email is usually the starting point of all phishing scams and it is also the easiest to fake and produce. Infosec IQ. To do so, go back to the previous tab and hover on top of the section that corresponds to your site.
Then, go back to the script and remove the facebook.com portion of the string inside the header function. Step 10. Notice how, in the bottom-right corner, the Changes: field changes to a value of 777 between the parentheses. An email is usually the starting point of all phishing scams and it is also the easiest to fake and produce. Infosec IQ. To do so, go back to the previous tab and hover on top of the section that corresponds to your site.
Do I misinterpret the results, or are my parameters the cause of this problem? You can send the crafted email to several recipients via adding email addresses to To, CC, and BCC fields. So now that you have permission to create the phishing website, and that weve established that you will not use it for any illegal activities; lets go ahead and actually show you how to build it. Social hacking tool, it will help you to hack social Accounts using fake login page.
Attackers frequently employ this method to steal usernames and passwords. Phishing is a form of fraud that attracts people and businesses to access malicious uniform resource locators (URLs) and submit their sensitive information such as passwords, credit card ids, and personal information. gets you full access to the PhishSim template library and education tools, but youll need to speak with an Infosec IQ representative for the ability to launch a free PhishSim campaign. git Support | Some important features are not available under community license, such as exporting campaign stats, performing file (attachment) attacks, and, most importantly, campaign scheduling options. WebEasyDMARCs phishing URL checker detects phishing and malicious websites. Next, open a text editor (were using Leafpad) and paste the source code you just copied.  WebTo do so, go back to the previous tab and hover on top of the section that corresponds to your site. WebThis phishing tutorial for cybersecurity pros explains phishing attacks; it covers the phishing pages concept and why it is the most dangerous cyberattack. Among all Cyber threats out there, phishing is probably the easiest kind of attack you can fall for. After removing the necessary Javascript functions and confirming the page loads, check to see if any images, css or other objects fail to load. Thats why we chose it to create the phishing script for our copy of Facebooks website. and then update the references for these to point to your copy of these files. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows bypassing 2-factor authentication protection. Phish JS - Universal phishing script with Telegram bot notification. One of the reasons our customers use CanIPhish is that we provide 30+ hosted phishing websites that can be used whenever you need them. Also, for privacy and security purposes, all the websites you see on this tutorial, as well as the 000webhost account I created for it, have been preemptively deleted right after taking the required screenshots.
WebTo do so, go back to the previous tab and hover on top of the section that corresponds to your site. WebThis phishing tutorial for cybersecurity pros explains phishing attacks; it covers the phishing pages concept and why it is the most dangerous cyberattack. Among all Cyber threats out there, phishing is probably the easiest kind of attack you can fall for. After removing the necessary Javascript functions and confirming the page loads, check to see if any images, css or other objects fail to load. Thats why we chose it to create the phishing script for our copy of Facebooks website. and then update the references for these to point to your copy of these files. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows bypassing 2-factor authentication protection. Phish JS - Universal phishing script with Telegram bot notification. One of the reasons our customers use CanIPhish is that we provide 30+ hosted phishing websites that can be used whenever you need them. Also, for privacy and security purposes, all the websites you see on this tutorial, as well as the 000webhost account I created for it, have been preemptively deleted right after taking the required screenshots. 
Generating Link for the Phishing Site We have a link to our phishing site now. No back door. Step 3. Genuine websites will never ask for your private information through email.